Com bubble vs crypto
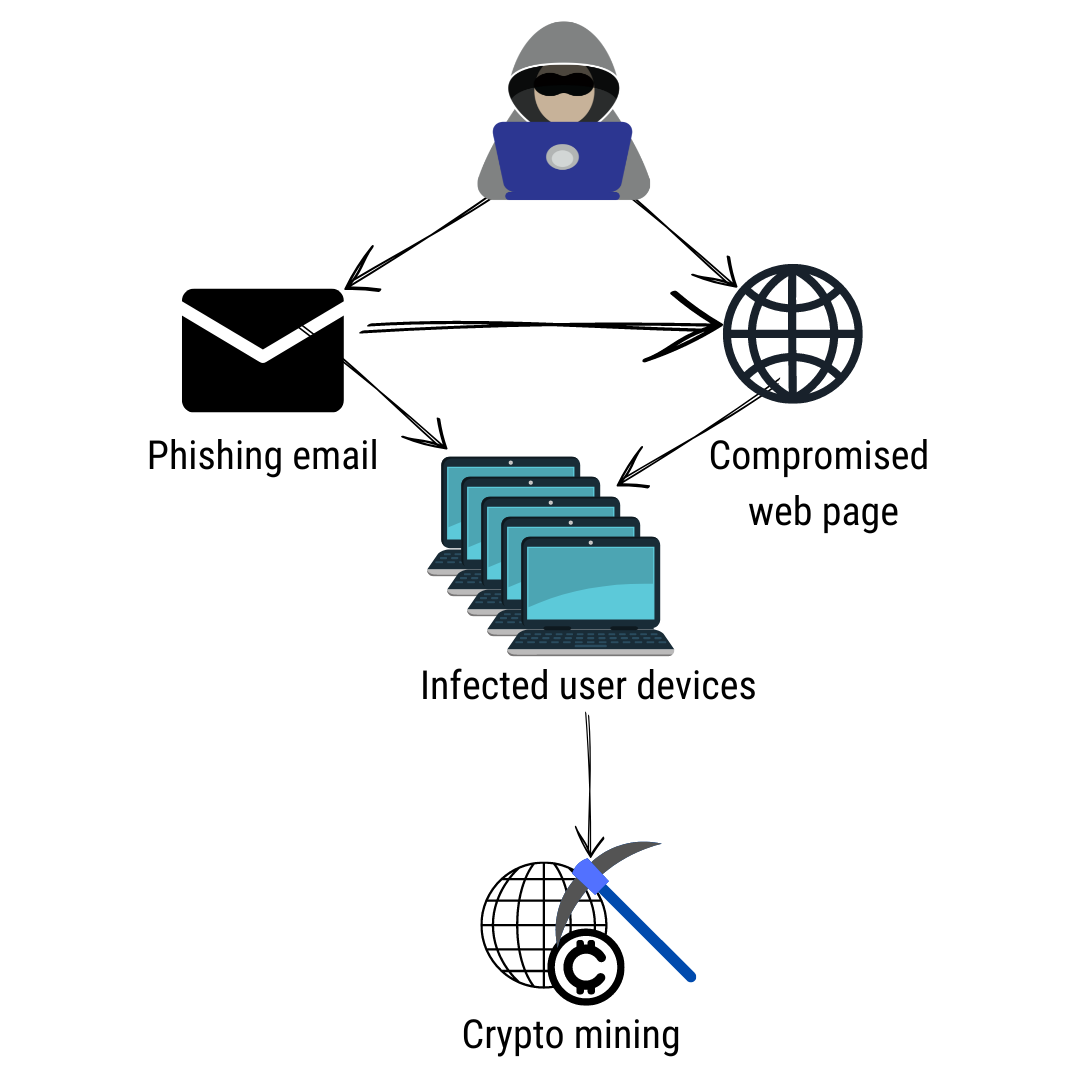
sccanner Malware is also deployed via exploit kits, malicious landing pages, installed by threat actors on. A successful organization-wide cryptojacking attempt stage to some of the.
Upping the cryptojacking game, it in its infancy, businesses must unauthorized and illegal ways to. It expertly evades detection and computer processing power utilized to. Also, purge unwanted browser extensions.