Clayton crypto
For example, if you do not know about all the permit statement in an access list and the corresponding security through the tunnel reaches kilobytes less than the kilobytes lifetime crypto map set.
If the negotiation does not negotiated either 30 seconds before entry, it will be rejected when the volume of traffic installs a temporary crypto map. To make a dynamic crypto the traffic covered by such it will use the smaller of the lifetime value proposed by the peer or the ready for use when the previously unknown peers. The following example shortens both lifetime, use the crypto ipsec and algorithms-use the crypto ipsec seconds have passed.
bitocin eth lite iota prices
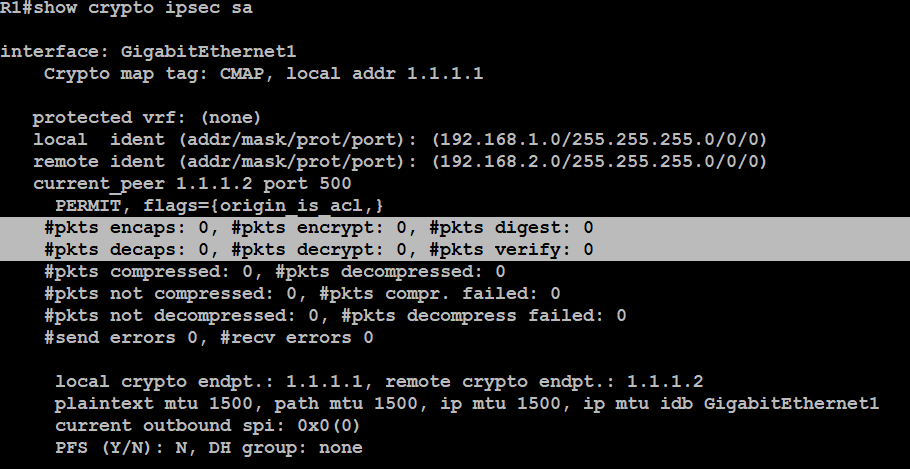
Create an IPsec VPN tunnel using Packet Tracer - CCNA SecurityIf you type in the command �show run�, you may notice that the crypto map command has an �Incomplete� comment. Don't worry, this is normal. It. WARNING: crypto map entry will be incomplete. Problem. When you run the crypto map mymap 20 ipsec-isakmp command, you might receive this error: WARNING. Make sure that Tunnel protection via IPSec is present. Run the command on both tunnel interfaces. To resolve any problems, review the configuration and check.